7667766266
enquiry@shankarias.in
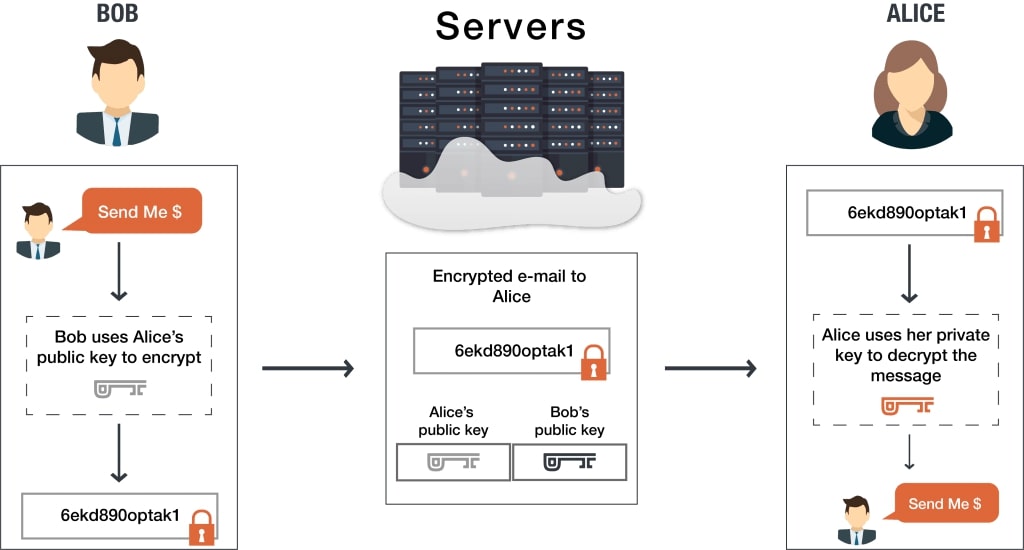
A recent announcement by messaging apps and technology giants to use end-to-end encryption to secure more user data has disappointed the government agencies.
References